PHP Tutorials
- What is MySqli
- mysql query
- mysql query example
- InnoDB
- mysql column Type
- CRUD Example
- Connection Using Function
- mysql keys
- SELECT
- WHERE
- UPDATE
- Count no of Rows
- ALIAS
- AND, AND & OR
- BETWEEN
- COMPARISON OPERATOR
- DELETE
- DELETE LIMIT
- DISTINCT
- EXISTS
- FROM
- GROUP BY
- HAVING
- IN
- INTERSECT
- IS NULL & IS NOT NULL
- LIKE
- NOT
- ORDER BY
- SELECT LIMIT
- SUBQUERY
- TRUNCATE
- UNION && UNION ALL
- Concat & Group_Concat
- mysql Function
- Mysql Insert Id
- MySql Aggregate Function
- Mysql Join
- JOIN in MySql
- Trigger
- Procedure
- Transaction
- views
- Index
- SQL Injection
- Normalization
- Query Bind
- Interview Questions
Important Link
what is SQL Injection in MySQL Database?
https://dotnettutorials.net/lesson/sql-injection-in-mysql/
SQL injection is a method where a malicious user can inject some SQL commands to display other information or destroy the database, using form fields on a web page or application.
it is possible to dynamically change SQL statements, and run some SQL commands which may display other user information or destroy the database. By using SQL injection, a hacker may get access to other users’ passwords and other sensitive information.
File Name :
Types of SQL Injection
There are mainly three types of SQL injections:
File Name :
1. SQL injections using 1=1
2. SQL injections using ""=""
3. SQL injection using batched SQL statements
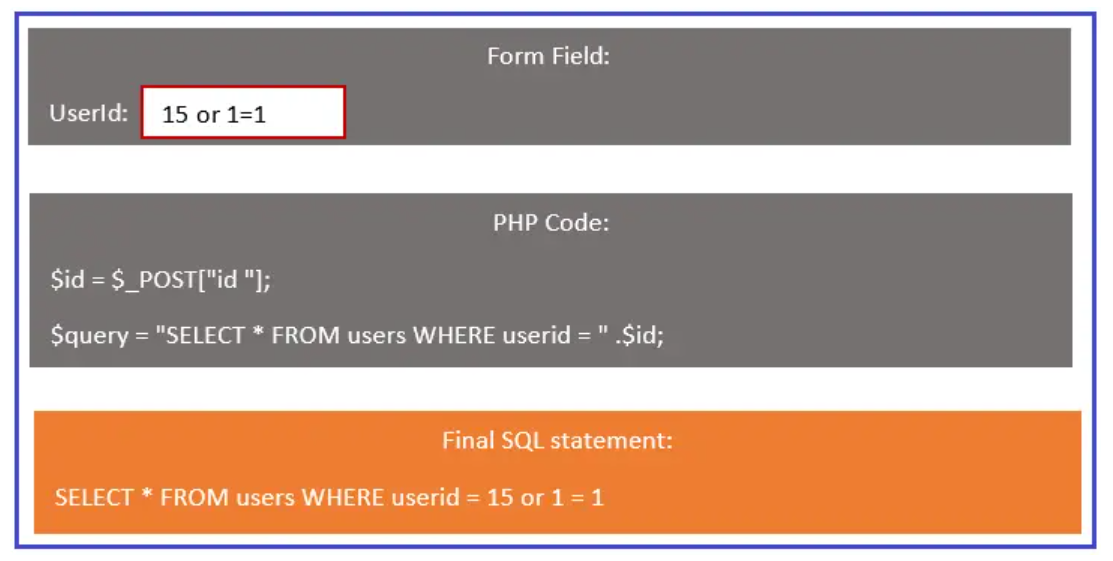
SQL injections using 1=1
the first box shows, form field where the malicious user is sending the value “15 or 1=1”. In the second box, PHP codes accept post variable value sent via a form field. The post variable value is stored in the $id variable, which is used in SQL queries to get user information. The third box shows the final SQL statement after replacing the $id value in PHP codes. Since the “1=1” condition is always TRUE, the malicious user can access all the user’s information. If the table contains a password data column, the password of other user accounts will be visible by using this SQL injection.
File Name :
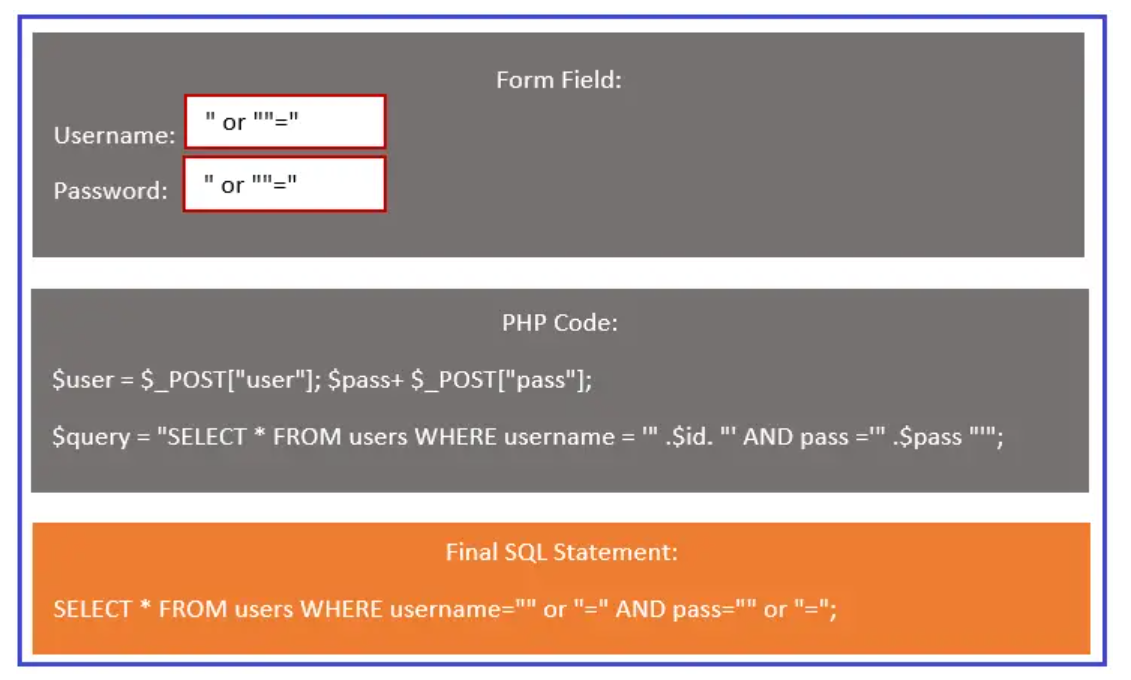
SQL injections using ""=""
The first box shows, form field where the malicious user is sending the username and password values as ” or “”=”. In the second box, the PHP code accepts the post variables value for username and password, and the values in $user and $pass variables. These variables are used in SQL queries to log in to the user’s account. The third box shows the final SQL statement after replacing the $user and $pass values in PHP codes. Since WHERE “”=”” is always true. The hacker will be able to get the information of all the users.
File Name :
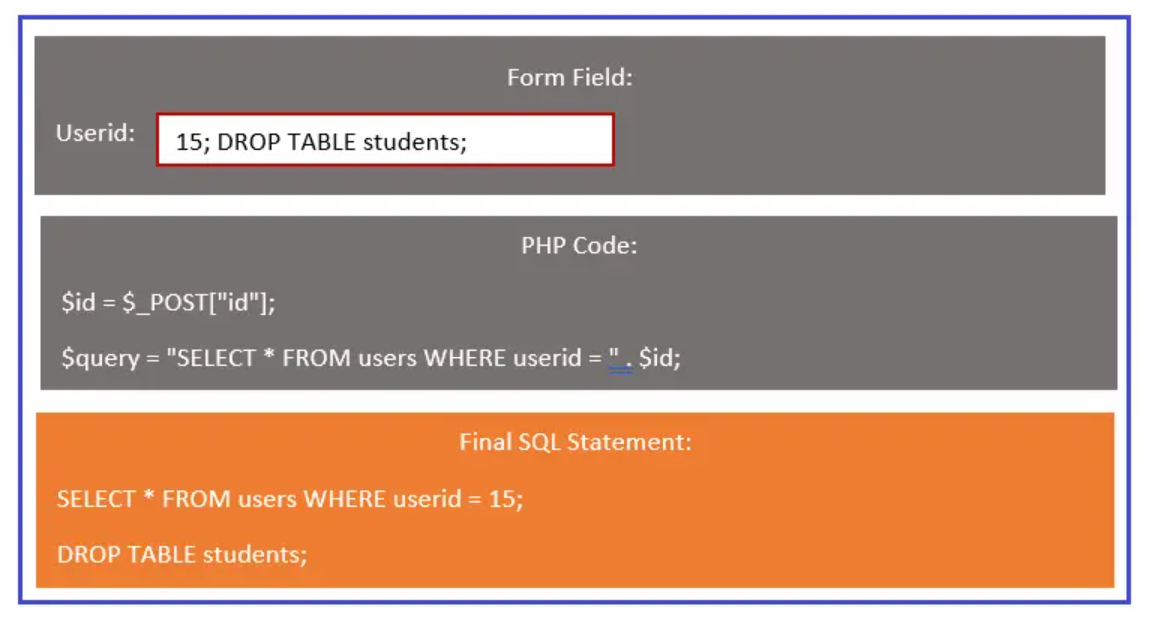
SQL Injections using batched statements
most of the databases supports executing multiple statements separated by semicolon. These statements are called batched SQL statements. The first box shows the form where the malicious user is sending the value 15; DROP TABLE students; In the second box, PHP codes accept post variable value sent via a form field. The post variable value is stored in the $id variable, which is used in SQL queries to get user information. The third box shows the final SQL statement after replacing the $id value in PHP codes. The SQL statement will display information of the userid 15 and then delete the table name ‘students’;
File Name :
SQL injection attacks
File Name :
Now suppose the statement for checking user id is: SELECT * FROM users WHERE email = $_POST[’email’] AND password = md5($_POST[‘password’]);
Now suppose the attacker provides the following input in the email address field:
input :- xxx@xxx.xxx’ OR 1 = 1 LIMIT 1 — ‘ ]
The SQL statement will be:
SELECT * FROM users WHERE email = ‘xxx@xxx.xxx’ OR 1 = 1 LIMIT 1 — ‘ ] AND password = md5(‘1234’);
Here, xxx@xxx.xxx ends with a single quote which completes the string quote, OR 1=1 LIMIT 1 is a condition that will always be true and limits the returned results to only one record & ‘AND is the SQL statement that eliminates the password part.